The idea that we should create a gargantuan list of cyber security tools started running through our minds a while ago because, in our journey into the cyber security and data protection world, we ran into lots of useful tools.
When we decided to work on this list, we had no idea how and where to begin.
What tools should we include? What should we not? How do we tell if one is worthy and the other one is not?
Do we mention ultra-known products?
Should we stick to what’s free or should we also add paid products?
Eventually, we came up with what we’re about to read. But first here’s a quick guideline that you should read before we jump right to the subject:
- We don’t claim this is the ultimate list. It’s not complete and it’s definitely not final. It probably never will be. We are aware that we missed lots of essential, important tools – by mistake or just because we can’t know them all. So please feel free to jump in with more useful tools that you feel they should be mentioned.
- We stayed away from recommending antivirus, VPN or firewall products. There are independent industry experts who only do that. Instead, we prefer to list those experts or websites that will help you compare such services, in order to choose what’s best for you
- We tried to test them all before recommending them. And we only included tools that have free versions.
Here’s our list :
50+ free security tools you can use for your online protection
Table of contents:
ACCOUNT & AUTHENTICATION MANAGEMENT
– Check if your password is strong
– Password managers
– Activate two-factor authentication
– Was your account hacked?
SOCIAL MEDIA SECURITY
– Geo-tag removal on social accounts
– Revoke access to third-party apps
– Do a security check-up
– Other communicating tools
SAFE BROWSING
– Keeping vulnerable software under control
– Extra Encryption, Privacy, and Anonymity
– Redirect checkers
– Remote screenshots
– Scan for threats
BACKUP, BACKUP, BACKUP
REPORTING
MISCELLANEOUS
Conclusion
– Check if your password is strong
– Password managers
– Activate two-factor authentication
– Was your account hacked?
SOCIAL MEDIA SECURITY
– Geo-tag removal on social accounts
– Revoke access to third-party apps
– Do a security check-up
– Other communicating tools
SAFE BROWSING
– Keeping vulnerable software under control
– Extra Encryption, Privacy, and Anonymity
– Redirect checkers
– Remote screenshots
– Scan for threats
BACKUP, BACKUP, BACKUP
REPORTING
MISCELLANEOUS
Conclusion
ACCOUNT & AUTHENTICATION MANAGEMENT

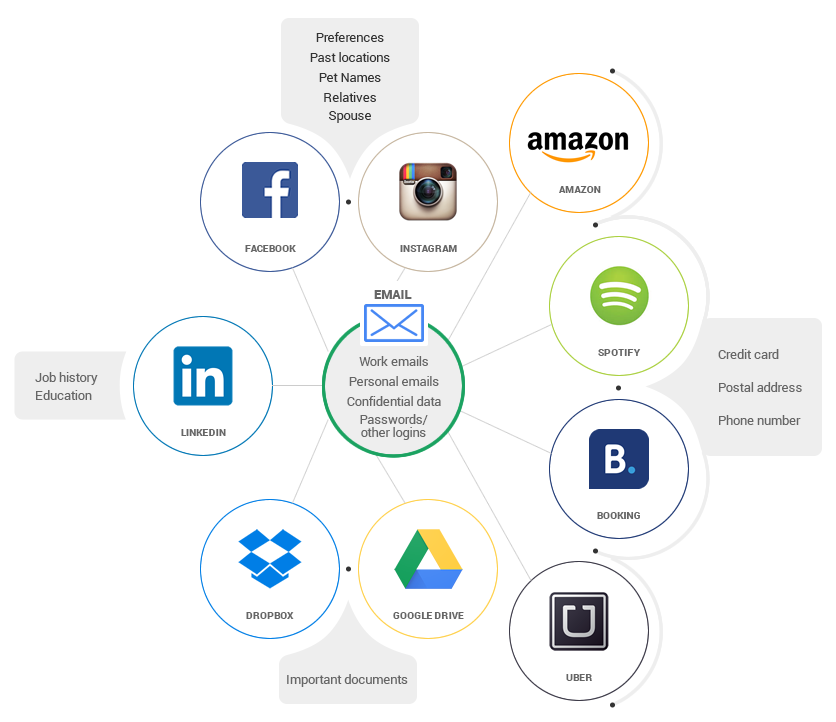
How strong is your password?
A unique and strong password is key to our online safety. We keep recommending this in our articles (and we’ll keep doing it) so people can realize the importance of setting passwords that hackers can’t reach.
First of all, here’s why it should be unique:
We never use the same key for our house and car, right? Then why would we use the same password for our accounts?
Our online accounts are interconnected. If one of those passwords is breached, the cyber criminal will have access to the rest of your accounts.
And no matter how careful you are not to give out your password, sometimes you might not be responsible for the breach. Companies have plenty of vulnerabilities. Their employees can have poor security habits. Their ex-employees might want to get vengeance this way. Your online connection might not be secure and your traffic unencrypted. There are tons of flaws out there that could expose your credentials.
Second of all, here’s why it should be strong (and what does “strong” mean):
Most people have weak passwords. They use family or pets names, favorite songs, birth dates and so on. This type of information nowadays is readily available online – usually posted directly by us, on social networks or blogs or forum comments.
If a cyber criminal really wants to hack your account and you use such a password, all they’ll have to do is spend some time finding out more information about you.
They also have the technical skills to test out millions of passwords combinations in a short period of time. So there’s that.
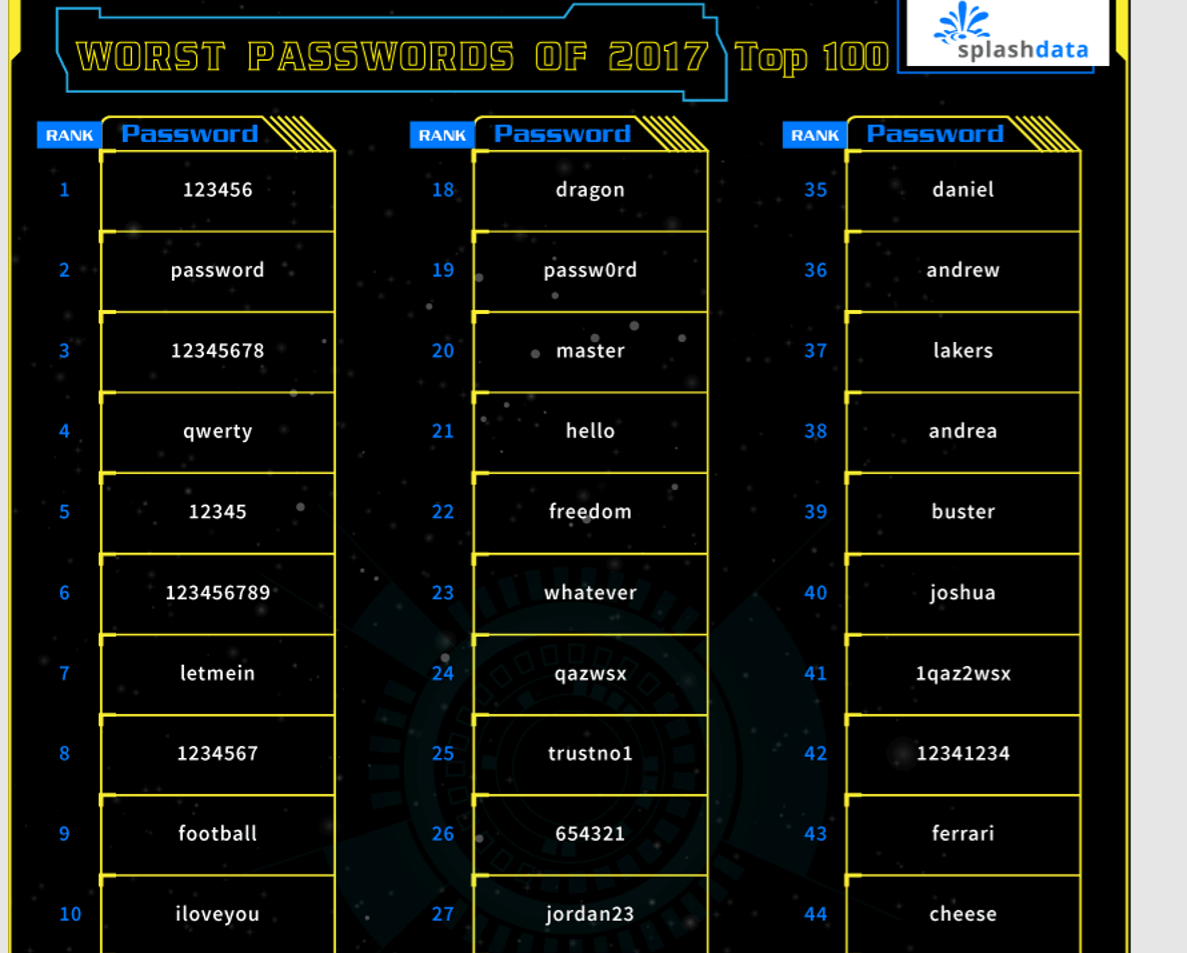
SplashData released its annual list of top worst passwords of 2017, where we see that people continue using the classic”123456″.
We strongly RECOMMEND using strong and unique passwords, and this step-by-step guidewill show you how to manage passwords like an expert.
And here are some tools that you can play with to find out how secure a password is considered (don’t test using your real passwords!).
Another great tool can estimate how long it would take for your password to be cracked by a hacker: Estimating Password-Cracking Times
Password managers
Constantly coming up with strong, unique passwords is hard. We get it.
It’s hard to remember to change them, and it’s even harder to remember them. Especially since it’s not recommended to write them down – not in a document on your desktop, not in an email draft, not in your phone or written on a paper that stays under your mouse pad. No, no, no, no.
And since not all of us have an elephant memory, some smart guys created tools that make it easier for us to manage passwords.
Passwords managers are easy to use. You install them as browsers plug-ins and they help us save passwords and keep them encrypted. When we log in to a new account, the password manager will ask us if we want to save the password.
All we have to do is remember the password that we use for the password manager tool account.
Here are some of the most popular apps for password management:
- LastPass – it’s one of the oldest and most known password managers.
- Sticky Password
- 1Password – not exactly free, but offers a free trial that lasts 30 days
Activate two-factor authentication
Ok, so this is plan B. If passwords fail and a cybercriminal somehow manages to find out your beautiful, strong, unique and completely random password, the second-factor authenticator will work as an extra shield.
Two-factor authentication adds an extra layer of protection. This way, the password will not be enough to access your account, you’ll also have to prove your identity using the second method. This usually consists of a unique, time-sensitive code, that you receive using your mobile phone.
In order not to do this every time you log into your account, you can choose to remember the devices you use and only require the second way of authentication when you want to log in from a new device (laptop, PC, tablet, browser, whatever that may be).
I always wonder why the companies don’t enable this option by default. It would help avoid a lot of accounts that end up compromised because of poor passwords habits.
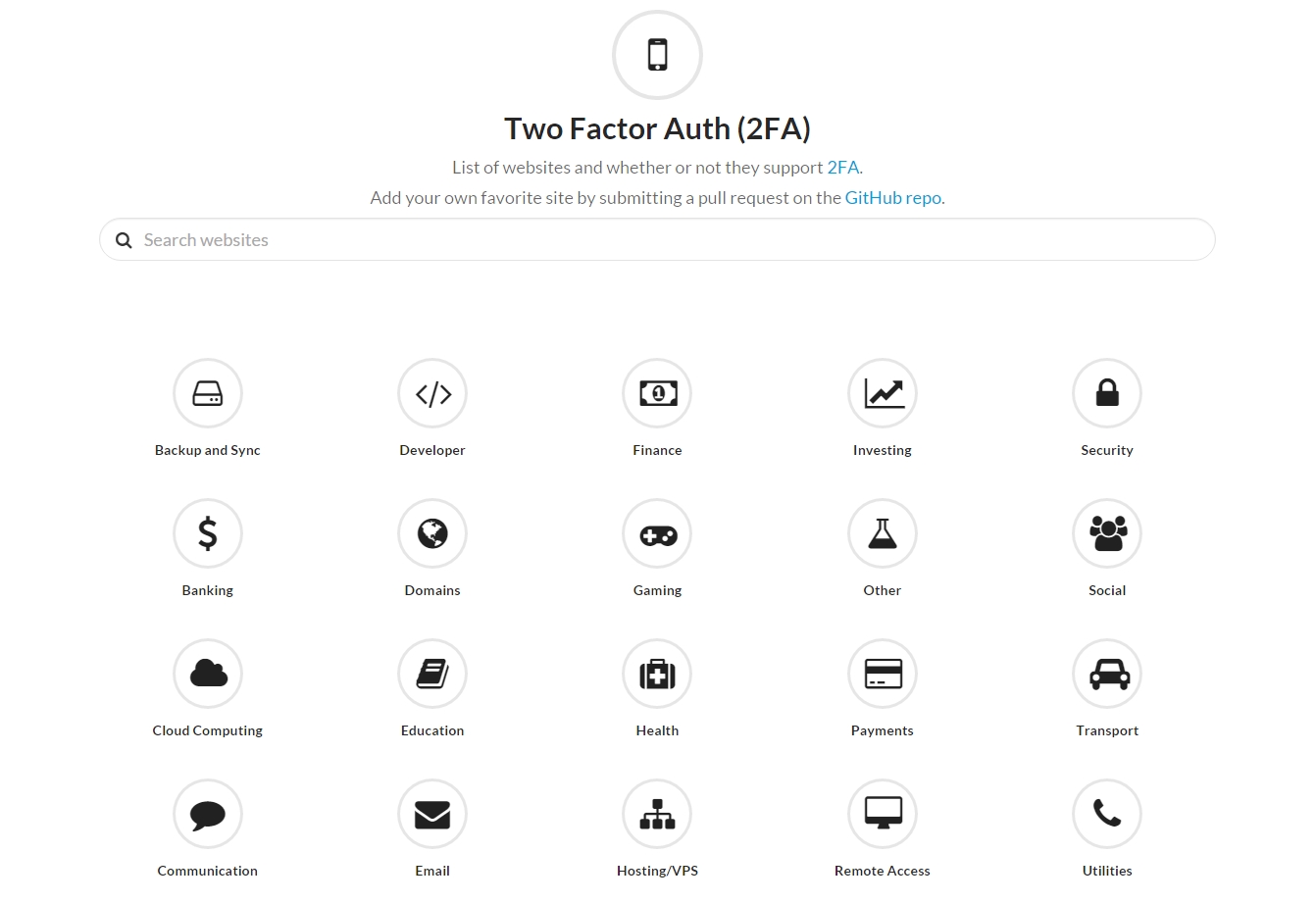
If you want to check what services offer users the possibility to activate two-factor authentication, use this tool:
Was your account hacked?
There are several projects out there that store a huge database of leaked, stolen or compromised passwords. Other projects gather all the past data breaches. You can use them to confront with your passwords or accounts and check their databases. If someone ever used a password that’s the same with yours and was leaked in a past breach, you’ll have to change it.
You can also check if you have any accounts that were compromised in any of those data breaches.
Use these services:
- Breach Alarm – for stolen passwords.
- have I been pwned? – for past breaches.
Here are more projects that you can use to inform yourself about data breaches:
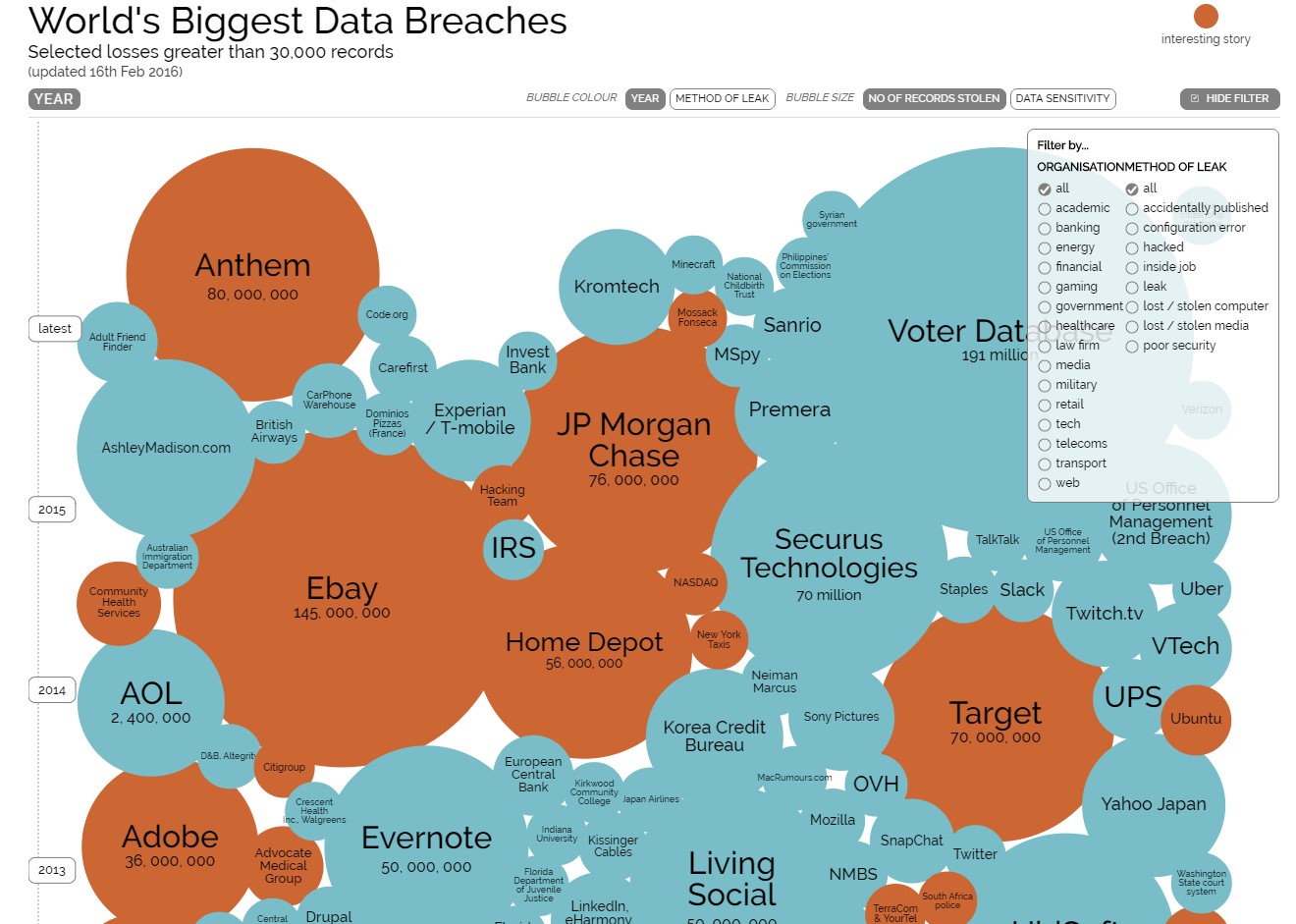
- World’s biggest data breaches – a great, visual tool.
- Data Breaches – a blog that gathers all data breaches, a “constant reminder that we are nowhere close to achieving adequate security”.
- Privacy Rights data breaches – a chronology list of data breaches since 2005.
Geo-tag removal on social accounts
It’s highly recommended that you avoid checking in from your social accounts – especially from your home.
Something so common and apparently innocent as a social media check-in can turn into a nightmare. You can never control who can access your social network posts. You never know who else benefits from the information you shared.
There have been many cases of people who checked in while on vacation, bragged about the wonderful places they visited, only to come back home and find out that they were robbed. Burglars were tipped off thanks to the posts on social media.
However, if it’s already too late and you already have plenty of check-ins made online, you can remove your previous ones.
For Facebook, you’ll have to do that manually for each post you published and then turn off location for future posts. However, for Instagram, there’s an easier batch solution that you can use.
Instagram is constantly updating its network and has changed the geo-map feature for mobile that let you control geotag location. Now you have the option to save photos you see and like on Instagram, save and add them to your photos collections.
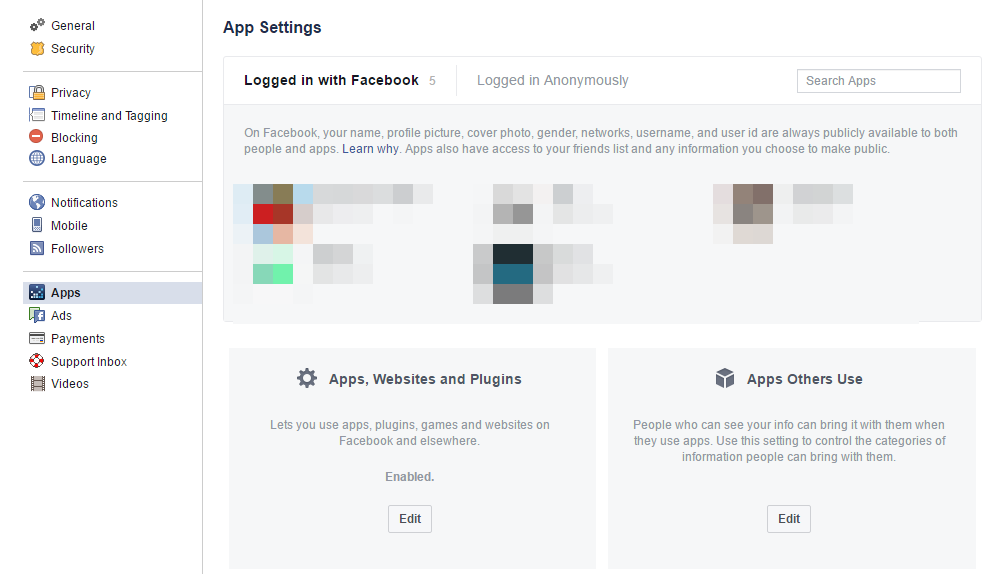
Revoke access to third-party apps
You probably logged in with your social accounts to any third-party apps – games, other social networks, streaming services and so on.
For privacy matters, it’s recommended that you only allow access to trustworthy apps. Those apps have access to your profiles and personal information.
From time to time, make sure you check every single app that you allowed to access your account and remove the ones that you don’t use anymore.
Here’s how you can remove access to external apps from every major social network:
- Revoke access on Facebook to third-party apps
- Revoke access on Twitter to third-party apps.
- Revoke access on Linkedin to third-party apps
- Revoke access on Instagram to third-party apps
Do a security check-up
Google and Facebook are among the networks that offer the possibility to do a security check-up. They will take you through the steps you need to check or activate in order to enhance your account’s protection.
Other communication tools
Here are other communicating tools that are focused on anonymity and encryption:
- Signal – free mobile app that you can use for encrypted communications (phone calls and messages). They also have a partnership with WhatsApp and helped them integrate end-to-end encryption.
- Off The Record – encrypted app used for instant messaging.
- Safe Pad – an online notepad that is encrypted end-to-end.
SAFE BROWSING
Keeping malicious software under control
There are some major software apps that are buggy and expose you to global cyber attacks. “Software” and “buggy” might just be pleonasms for the moment, as all software have bugs and vulnerabilities.
What you should bear in mind is that you can reduce your odds of being infected just by keeping those buggy apps up to date. Or disabled until you really need them and activate them punctually. Or uninstalled, if they aren’t vital to your work.
By “apps” we mean browsers, plug-ins, add-ons. Chrome, Firefox, Flash Player, Java, and Adobe Reader, just to name a few of them, but you should take a look over the infographic published here to find out more about the top most vulnerable apps.
Here’s how you can reduce your odds of getting infected:
1. Keep those vital apps up to date. You can use an automated patching tool that will take care of that for you, silently (Heimdal FREE does that).
2. Use a tool that will scan your traffic and restrict your access to infected web pages (our product also does that, and also makes sure that none of your data goes out to the bad guys).
3. No clicking on suspicious links or attachments, short links that you don’t know where they’ll lead you, nothing that you never requested or sounds fishy (even if it’s coming from your online buddies). Staying away from dangerous web locations also is vital (that means no websites that host illegal content, such as torrents).
4. Keep activated a good, trustworthy antivirus. Here’s how to choose it.
5. Use an app that will block those plug-ins and apps.
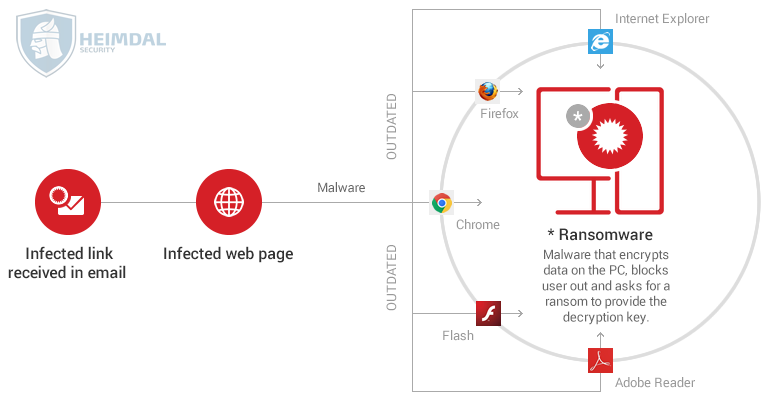
You can see in the infographic below how a global ransomware infects your operating system:
Some tools that will come in handy:
- AdBlock – you’ll get rid of annoying ads, but you’ll also reduce your chances of ending up with spreading ransomware from malvertising.
- NoScript – an add-on for Firefox that allows plugins to be executed only by trusted web sites of your choice.
- Script Safe – same as NoScript, but for Chrome.
- Flashblock – Firefox add-on that blocks Flash
- Flash control – Chrome add-on that lets you take more control over Flash
- Dragon Internet Browser – a free tool based on Chromium technology that will provide a higher level of protection
- Google Chrome Cleanup Tool – this app will scan and remove software that can cause problems with Chrome browser
Extra Encryption, Privacy, and Anonymity
If you want extra anonymity, here is a list of tools that are focused on encryption and privacy:
- Tor Project – we’re sure you already know about this one. You can use Tor to browse the web while staying anonymous.
- Comparison VPN – the name is pretty much self-explanatory, right? “VPN” comes from “Virtual Private Network” and it’s used to encrypt your outgoing and ongoing traffic. This tool will help you compare between different VPN services.
- Duck Duck Go – it’s a free search engine but, unlike others, it doesn’t track you, doesn’t collect or share any of your personal information.
- Disconnect – the basic version will block trackers from websites.
- uBlock – a lightweight free and open source browser extension that will help you filter our annoying or unwanted content, such as tracking cookies and ads (available for Mozilla, Chrome, Safari and even Microsoft Edge).
- Https everywhere – it’s an extension for your browser that encrypts your communications with major websites; resulted in a collaboration between The Tor Projectand the Electronic Frontier Foundation.
- Ghostery – a free browser extension that lets you control trackers from the websites that you visit.
Redirect checkers
If you want to avoid any phishing or malware attacks, it’s best that you don’t click on any links that you don’t know where they’ll lead you. They might be links shortened using services such as Bit.ly or Unshorten or links that look similar to perfectly legitimate ones but use a variation in spelling or domain.
Use one of these services to check where a link will redirect you:
Other dedicated and useful tools that you can use to detect links to malware websites:
- http://www.checkshorturl.com/
- http://www.getlinkinfo.com/
- http://untiny.com/
- http://www.linkexpander.com/
Remote screenshots
As an alternative to remotely check where a short link will take you, you can also use a service that remotely takes screenshots of a given website.
This kind of services are usually used by developers, to see how a website will look on different resolutions and browsers used by users, but they can also come in handy when it comes to Internet security.
This way, you’ll see how a website looks like and where you’ll end up if you click on that link, without actually visiting it.
You can use one of these services:
Scan for advanced threats
There are services that will help you check if a website has been reported for phishing, malicious code, unwanted software or has a poor reputation. This way, you’ll know to avoid it.
You can check using one of these:
- Virus Total (it also lets you upload and scan files)
- ScanURL
- URL Query
- URL Checker
- Site Safety Center
- Trusted Source
- Zulu Scaler
- Sucuri
- Quttera
- PhishTank
You can also find useful this list of free online anti-malware scanners.
BACKUP, BACKUP, BACKUP
How valuable are the work documents that you keep on your desktop, your email or in the cloud?
What about your collection of photos or private conversations? Would you miss them if they were ever deleted or lost?
What if they were stolen? Or, even worse, encrypted in a ransomware attack?
Stop telling yourself “it can’t happen to me”. The odds for ending up with malware attacks are against you.
And most of these attacks are automated, nobody hand picks you as a victim. It’s enough for you to have files and outdated browsers, plugins or apps. You don’t even have to click or download anything to end up infected – nowadays you can be compromised even on perfectly legit websites.
For example, BBC, The New York Times and AOL were recently hit with a malvertising campaign that delivered notable ransomware to users.
Bad news is that even if you pay the ransom, there’s no guarantee that you’ll receive the encryption key to gain back access to your files. Or the encryption might have gone wrong and corrupted the files. It’s one of the reasons why the FBI advises against paying the ransom.
Let’s not forget about the recent cyber attacks (WannaCry, Petya ransomware) impacting big organizations and institutions (Telefonica, Renault, FedEx, the National Health Service (NHS) in England and Scotland, Maersk, Government of Ukraine, and many more) that saw their computers compromised and lost access to valuable information.
No matter how many Internet security layers you have in place, always have a backup. Set in place at least two automatic backups. If everything else fails, at least you’ll be covered.
It’s not complicated to set them up, you don’t need advanced tech skills. Our colleague Andra explained in a separate blog article how you can easily backup your data.
And here are two more tools that will help you out:
- Best Backup – helps you choose the backup solutions suited to your needs
- Spider Oak – backup solution focused on encryption and Internet security
REPORTING
Although ignored by most people, this step is also important to cyber security. Take your time and file a report if you run into anything that looks fishy.
If you have a hunch that something is wrong and you might have fallen into a trap, immediately contact your bank or credit card institution and close the accounts you believe they may have been compromised.
If this is not the case and you simply ran into spam, scams or phishing attempts, it’s best that you report them to government organizations or even cyber security companies.
Here are some of the places where you can do that:
- On Guard Online – report spam
- Google – report spam
- Scamwatch.gov.au – report scam
- Scamadviser – check how safe is a website before you buy from it
- US-Cert.gov – report phishing
- Consumer.ftc.gov – report phishing
- Google – report phishing or badware
- Plain Text Offenders – report those who send you the password in plain text
MISCELLANEOUS
A few tools that didn’t fit into any other major category, but we also wanted to mention them.
- Eraser – Windows tool that allows you to completely remove data from your hard drive, by overwriting it several times.
- Cvedetails.com – check how many vulnerabilities your favorite apps have and how severe they are..
- Header Analysis – analyse email header. And here’s how you can read the header details.
- Free Shredder Software Programs – A very useful list of 36 free software tools that will help you delete files on your computer.
- Site Safety – A tool that helps you identify whether a site is safe or not
- Deseat.me – It help you clean up your online presence
- IP Feeds – This tool analyzes all security IP Feeds that are related to online attacks
- WhatisMyBrowser – An online service providing data about your browser’s capabilities.
- Scrim – This tool helps you convert your email address into a short and safe link
We also recommend checking these resources to help you update your Internet security knowledge:
- What to know about identity theft
- Network and Information Security quiz
- CyberSecurity Quizzes & Test – A list of useful online quizzes for testing your theoretical and practical information on this topic.
For the ones with advanced technical skills, here are some tools that show vulnerabilities in software:
Conclusion
In the cyber security game, the good guys and the bad ones constantly try to outrun each other. That’s why you should always remember that no tool is bulletproof. Don’t rely exclusively on a software or an app to keep you safe, as they all have flaws and vulnerabilities.
Instead, try to think and act like a journalist. Question everything that you receive or run into in the digital world, even if it only looks slightly suspicious. Triple check it before you act on it, be sure that you don’t throw yourself into anything fishy.
Continue to improve your cyber education. In time, you’ll train your intuition and it will become increasingly easier to spot potential compromises.
It’s essential that you never give up on healthy Internet security habits. Add as many security layers as possible – onion style – in order to decrease the impact of a potential attack.









Selling USA FRESH SSN Leads/Fullz, along with Driving License/ID Number with good connectivity.
ReplyDelete**Price for One SSN lead 2$**
All SSN's are Tested & Verified. Fresh spammed data.
**DETAILS IN LEADS/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL
->EMPLOYEE DETAILS
->Bulk order negotiable
->Hope for the long term business
->You can asked for specific states too
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040