Let’s get this clear first: identity theft is the illegal use of someone’s personal information. An impostor can steal your data and then use it to make financial operations. They can use your credit card details, can open bank accounts in your name, take out loans, ruin your credit card’s rating and many others.You might think that you can’t be affected by this, but it’s actually a common type of fraud.
According to the Federal Trade Commission‘s annual report on 2015, identity theft still tops the consumer complaints:
“Identity theft complaints were the second most reported, increasing more than 47 percent percent from 2014 on the back of a massive jump in complaints about tax identity theft from consumers. Identity theft complaints had been the top category for the previous 15 years. Imposter scams – in which scammers impersonate someone else to commit fraud – remained the third-most common complaint in 2015.”
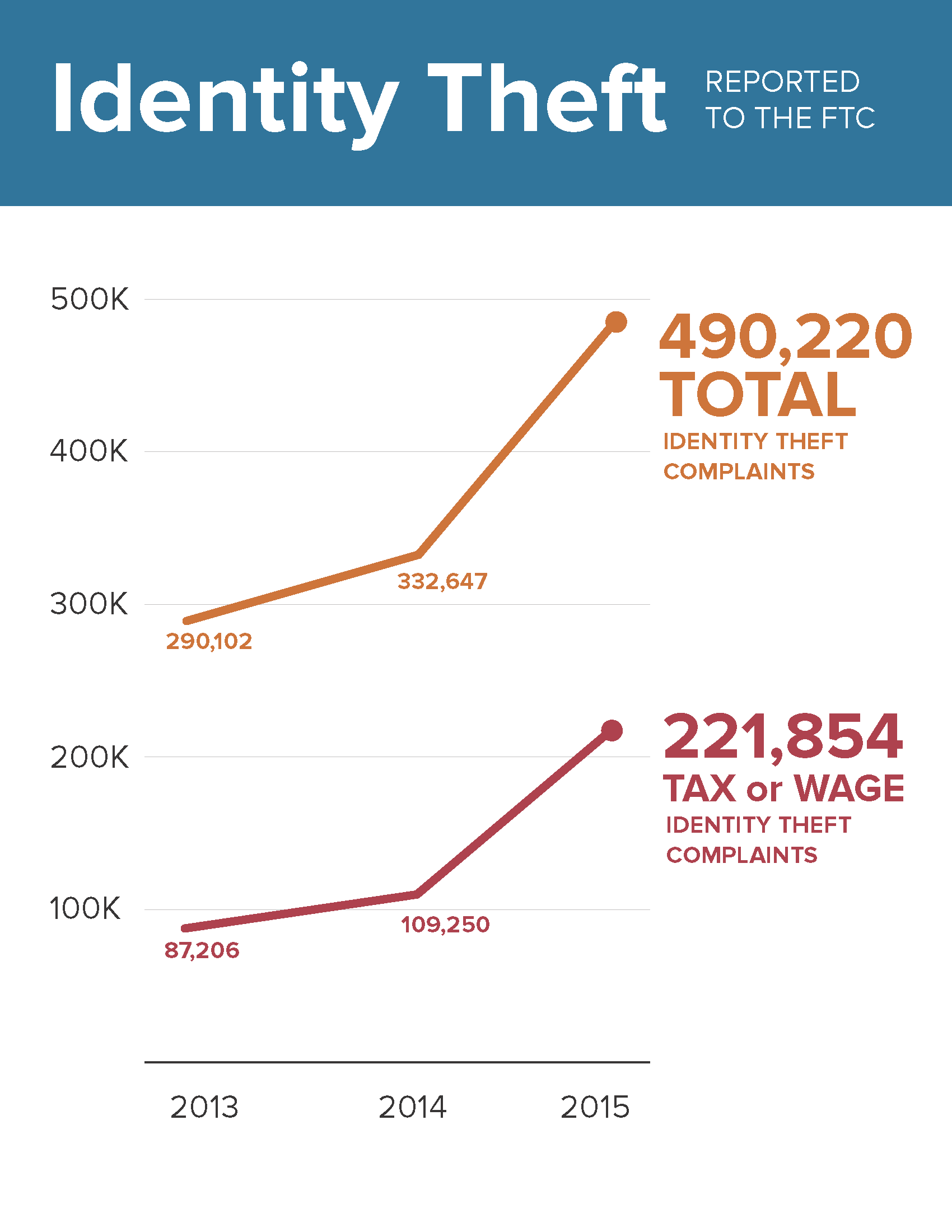
In the U.S., the average annual number of identity fraud victims is around 12 million, with a total financial loss of $26,350,000,000 (more statistics here).
Besides the financial loss, there may be additional consequences if that person is held responsible for criminal actions.
There are also other types of identity theft, such as medical, but we’ll focus on the financial part mostly.
What’s scarier is that 68% of the victims don’t even know how the thief obtained their information in the first place and 92% know nothing about the individual or group that stole from them (more statistics in the infographic published by Identity Force).
How to prevent identity theft from criminals
As Bruce Schneier said in Mitigating Identity Theft:
“Identity theft is the new crime of the information age. A criminal collects enough personal data on someone to impersonate a victim to banks, credit card companies, and other financial institutions. Then he racks up debt in the person’s name, collects the cash, and disappears. The victim is left holding the bag. While some of the losses are absorbed by financial institutions — credit card companies in particular — the credit-rating damage is borne by the victim. It can take years for the victim to clear his name.”
Once identity theft occurs, it is extremely difficult to recover the information that cybercriminals have stolen. Many times, you aren’t even aware of how or when it happened.
That’s why it’s always better to take proactive security measures, that will prevent fraudsters from stealing your personal details and information. It’s easier to play it safe instead of only react once the damage is done and it’s too late to keep it under control.
Protect From Online Threats

1. Choose a good password for your online accounts
It’s a long way between knowing what’s good for us and actually taking the right measures. That’s why we insist on the strong passwords step: it’s an essential one, that you shouldn’t skip.
Make sure that your passwords are strong and unique.
Make them around 15 characters long, use both uppercase and lowercase letters, use numbers and symbols.
Don’t use your birth date, phone number, social security number, family members name or your pet’s name – these can be easily guessed by a cyber attacker, usually just by looking over your social profiles.
It’s also important that you don’t reuse passwords between your accounts.
Major breaches might occur, such as the recent ones that involved LinkedIn, MySpace and Tumblr, where hundreds of accounts details went for sale on the dark web. If you used the same pass everywhere, attackers will be able to access all of your other accounts.
But how exactly are we supposed to do this, if we create so many online accounts?
First of all, don’t write them down – not on a paper on your desk, not in an email draft, not on a text file that you leave on your desktop. Those are unsafe location.
Instead, you can start using a password manager, such as LastPass. It will remember all your passwords and store them in a secure way. This way, you’ll only have to remember one master password, the one for your main LastPass account.
Another key security step is to activate the two-factor authentication wherever it’s available.
Here are more tips on securing your passwords.
2. Don’t post confidential information online
Think twice before publishing information about you. Everything that we post online will remain there and be available for everyone who wants to see it.
As much as we’d like to think that we have control over our privacy, the truth is we can never be sure who’s watching us. We will never know where that information will end up. Even if we take all the possible security measures, we still depend on other services and systems, that might not be as safe as they claim they are.
That’s why it’s important that we pay attention to all the data that we place in comments, private messages, posts, check-ins, photos or anything else that we display online.
And by “online” we mean posts, photos, check-ins or comments on blogs, social networks (Twitter, Facebook, LinkedIn, Instagram, etc), but also websites such as AirBnB, TripAdvisor, Booking and so on.
Be paranoid. Protect your data like everyone’s watching you – because they really might be!
Which leads us to the next step…
3. Think twice before you post personal information about you on social networks
There is no discussion that social media is an important part of our lives. Especially nowadays, when all our friends, work colleagues or family members have Facebook accounts. It’s the one place where we can find almost anyone.
This leads to an increasing danger for our personal information, since it’s a blurred line between what’s public and what’s private.
No matter how careful you are with the privacy settings, you can never fully be in control.
How much do you share?

4. Watch out for phishing scams
Phishing is one of the oldest cyber threats, but it still causes a lot of damage. Attackers have constantly improved their techniques and fraud methods.
The main phishing schemes and campaigns appear when:
- we shop online
- we check our email account
- access social media networks
Though phishing uses multiple channels to get our credentials, email spam campaigns remain the main successful method.
The Verizon Data Breach Investigation Report shows that 23% of email recipients open phishing messages, and 11% click on attachments. That means they are three times more effective than legit email campaigns conducted nowadays.
Therefore, make sure you read our guide on how phishing works and how you can detect it.

5. Be careful when you shop online
The online medium is extremely convenient when it comes to shopping. We have more options than ever in just one place, one click away, saving us lots of time and money.
But how can you know that you buy from a legitimate website?
Follow these steps to make sure you don’t send your financial details to cybercriminals:
- It’s generally best if you shop from known, trusted websites. This will reduce any odds of unpleasant surprises.
- Check if the connection is encrypted. You can do this by looking at the address bar: is there an icon of a green lock? Does the address start with “https” instead of “http”? The extra “s” means that the website has SSL certificate (Secure Socket Layer).
- Also make sure that you activate a second-authentication factor when paying online. You will receive a final identification code on your phone before placing the order.
- Safest way to go: use a separate card just for online shopping. Transfer money on it only when you want to buy something, otherwise keep it with a low amount on it (for maintenance taxes). This way, in case something bad happens, you still have a safety net.
We also need to teach our children and / or parents that online actions have real consequences. Using credit cards on any website, without checking it first, poses serious privacy risks.

6. Secure your browser settings
Our browser is the main tool we use to connect to websites.
For this reason, an important degree of attention needs to be given to it. We’ll take you through a basic checklist:
- Are you using the latest version for your browser? Make sure you have the last browser version that contains all the available security patches.
- Use a private browsing session if you connect from a public computer. You don’t want your browsing history details to be recorded locally.
- To make sure your connection is safe, you can encrypt it using VPN software or Tor browser. It hides your browsing activity by routing your traffic through the Tor network of computers.
Here are more tips on how to improve your browser’s security settings.
7. Protect your computer with multiple security products
Identity thieves use multiple tools to get to your personal data. We are not talking about classical viruses here, we refer to advanced malware and spyware tools, such as keyloggers, exploit kits and remote administration tools. These are capable to retrieve sensitive information from a system without your knowledge.
Advanced malware is designed to evade normal antivirus detection. Sometimes a long time will pass until you become aware of its presence.
So, how do you choose the best antivirus that can keep online criminals away from your target machine? And is that enough?
8. Use a specialized security solution against financial and data stealing malware
Traditional security solutions may not be able to fight advanced pieces of code developed by cyber-criminal minds.
To assure financial security for banking operations and protection against zero day malware, you need an advanced scanning technology that can protect you from the latest threats.
9. Keep your operating system safe from spyware
Spyware is a type of software capable of installing on your computer in order to launch pop-up windows, redirect your browser to malicious locations and monitor your browsing sessions and your overall internet connection.
To stay safe from spyware, you can use one of the popular anti-spyware products available. A few security solutions capable of removing spyware from your system are Malwarebytes, Spybot Search and Destroy or Lavasoft’s Ad-Aware.
10. Keep your system and software up-to-date
Keep your system up-to-date with the latest security patches available. The same thing you should do for your vulnerable applications and programs.
This will cover any security hole that appears.
If you don’t want to bother checking and keeping those apps up-to-date every day, you can also use a free dedicated solution to do the job.
Protect From Physical Threats

The following steps will help you stay protected from the physical identity theft attempts.
11. Who’s watching you?
You are in front of an ATM machine or at the local shop and try to withdraw some money or just insert your PIN to pay.
Did you consider hiding your personal identification numbers or your bank account details from a possible privacy breach?
Before placing your sensitive data, look around and make sure there’s no one looking suspicious or who stays too close to see your information.
Ok, did you look?
Even if you don’t see anyone around, there may still be thieves that use special surveillance mechanisms. So just to make sure you are on the safe side, try to hide the numbers you insert.

12. What do you carry with you?
So many times you go out for a walk or for a dinner in the evening. Maybe you go to see a friend or just watch a new movie at the cinema.
Do you really need to carry with you all the credit cards and your official papers?
Before you leave your home, just think a bit if you need all those things with you. Take only the necessary – in case you lose them or forget them somewhere, you’ll limit the potential loss.
Before you leave your home, just think a bit if you need all those things with you. Take only the necessary – in case you lose them or forget them somewhere, you’ll limit the potential loss.
If you really need to carry your valuable credit cards, your ID or maybe your passport, where are you keeping them? How do you carry them around?
To limit the potential loss, follow these steps:
- Don’t leave your bag unattended in a public place or place it far from you. If a thief takes your bag, can you catch him in time?
- Don’t leave your wallet or purse in a jacket just hanging around. Don’t make things easy for a thief.
- Imagine that your wallet or bag have been stolen. How much did you lose? What are the actions you need to take to retrieve your official papers? Do you have the bank phone number to call for a potential block? Make sure you know the answers to these questions especially when you travel.
- Consider distraction elements for the thieves. You can keep a fake wallet or simply don’t place important things in the bag that can be stolen. Keep the important stuff close to you.
13. Destroy any documents or papers you don’t need anymore
We all keep important data in our homes. It can be information from past work places, medical records, certifications and diplomas, maybe even confidential information related to your work.
We all have the tendency to collect various papers and pieces of information. Some of them we might not actually need anymore, such as receipts or bank statements.
Though we may not need that data anymore, it doesn’t mean that for fraudsters it’s not an important element that can be used.
Make sure you destroy those papers before you throw them away. Don’t just place them in a garbage can – use a shredder.

14. Protect your normal mailbox
Try to think like an identity thief. You need to find personal information, especially financial details about someone. How do you do it? Where do you start from?
The easiest way is to start with those less protected areas, such as the mailbox. And now that you know where they will attack, just think about it:
What type of information do you receive in the mail box? Do you receive important documents from the bank, maybe the next credit card? If you do, you need to contact the bank and have them stop this type of correspondence. If you have important stuff you need to collect, just go to the bank and pick it up.
Do you receive invoices for every service in the house? Maybe it doesn’t seem like too much data for you, but an identity thief can use this information to correlate it to other sources in order to have an image on your financial situation. It would be easier to receive the invoices by email, since today most services providers offer this option.
How well did you secure your mail box? If anyone can access your mailbox and you know that vital information is delivered there, probably you should get a high security locking mailbox or a personal one in the post office.

15. Do you know who’s calling?
Yes, an identity thief may call you, posing as a bank agent or official representative and ask for private details or financial data.
How does the thief know what’s your bank? Well, keep in mind the previous points. Itsn’t not that hard to obtain information about you.
They may look through your mail box, they may watch you at the shop or at the ATM, or they may even look through your garbage. It is not difficult to discover this piece of information.
And don’t be fooled by the professional tone they use or the fact that you’re talking to a nice woman. This criminal profession knows no limits. Therefore, do not provide important information over the phone, unless you initiated the phone call and you really know who you’re talking to.
16. Destroy your digital information
Nowadays we all use cloud services to store our important files, no matter if they are work documents or personal photos.
However, along the years we collected various types of information on CDs, DVDs or external hard drives. And sometimes, we have been forced to throw into thrash a hard disk which didn’t seem to work anymore, without thinking about the private data we left on it.
To understand how the information from an abandoned disk can harm you, just think about all the photos, documents and private details you left on them.
Using special tools and software, a hacker who finds such a disk can retrieve all that information easily and use it against you – even if you deleted it and formated it before throwing it.

To make sure that an insecure disposal of old disks doesn’t become an opportunity for identity thieves, you need to be sure that you destroyed that data.
The following options are available:
- Overwrite the data a few times and make things a bit more difficult for an identity thief. You can also use specialized software that will do this for you.
- Physically destroy that hard disk or that CD/DVD.
- Did you know printers and photocopiers also have hard disk built in? So don’t just throw away that printer before removing the hard disk first.
17. Protect your Social Security number
This is one of the most important steps you need to take to protect your identity from thieves, since this piece of information can be used in multiple situations.
An identity thief can use your social security number to apply for a new credit card or open a bank account, ask for a loan or rent a house.
It can also be used to prove your identity over the phone or online, in order to access private information.
Here are a few techniques to protect it:
- Don’t use it as a password on any online account.
- Don’t just take it with you anywhere, unless you really need it.
- Don’t send it over the email.
- Don’t store it on your computer, your smartphone or your cloud drive.

18. Keep your smartphone safe
Nowadays we can do all our work just by using smartphones.
We use them to take pictures, to stay informed, to keep in touch to our friends, to access our cloud storage or even run financial transactions.
And this becomes our greatest risk. Just think about the amount of information one can gain just by accessing our smartphone.
That’s why we need to underline a few steps you can follow to make sure your smartphone’s data doesn’t fall into the wrong hands:
- Download apps from well known companies, especially apps that are used for financial transactions.
- Physically watch your smartphone and instruct your children on this too. Just by gaining access to your smartphone, an identity thief obtains a large amount of information.
- Secure the mobile device with a strong password or better yet, use 2 methods to keep it sealed from any breach. Biometric authentication, such as locking it with your fingerprint, is the most secure one.
- Use the best apps available to protect your smartphone. Most of them include a GPS feature and a remote wipe out mechanism.
Here’s an extended guide on how to keep your smartphone secure.

19. Check your bank account transactions daily
You think you know what purchases you have operated that month, you might even have SMS alerts activated. However, cyber criminals always find ways to steal just small amount of money, in order to test your attention.
There are so many cases where customers’ credit card information has been “read” and used in restaurants and stores, only to find out later about this, when it was already too late.
A good idea is to activate on your bank account the option to receive alerts for any sum of money that has been retrieved.
And make sure you know the bank’s policy on this type of cases, so that you know what’s next if your card is under attack.
20. Back it up
We don’t mean the computer back-up now, but the idea of backing something up is to accept that a certain thing may be lost at some moment.
Let’s try to answer a few questions so that we may solve this problem:
- Are you keeping all your money on one credit card? Why? Use at least two and split the money between them.
- Do you carry both cards with you when you go out? Why? Just take one. Or at least don’t place them both in the same place. This way, you’ll limit the potential loss.
- Do you need to verify your identity somewhere? Ok, take an identification paper or document with you, but don’t take the ID, the driver license and the passport along.
- And do you really need an official document with you? Maybe you can replace it with a photocopy. In any case, make sure you always have photocopies for all the important documents, especially when travelling.
- Do you have a phone number where you can call for help in case you lose an official paper or the credit card?

Conclusion
We tried to cover every possible situation that may appear, from the online threats commonly used by cyber attackers, to the physical ones that you expose ourselves to.
The idea behind all this is quite simple: always hope for the best, but prepare for the worst. Imagine all possible situations. Know what you’ll have to do in case the worst scenario comes true.
Did you ever have to deal with an identity theft attempt? How did it happen and what did you do to control the damage?


Selling USA FRESH SSN Leads/Fullz, along with Driving License/ID Number with good connectivity.
ReplyDelete**Price for One SSN lead 2$**
All SSN's are Tested & Verified. Fresh spammed data.
**DETAILS IN LEADS/FULLZ**
->FULL NAME
->SSN
->DATE OF BIRTH
->DRIVING LICENSE NUMBER
->ADDRESS WITH ZIP
->PHONE NUMBER, EMAIL
->EMPLOYEE DETAILS
->Bulk order negotiable
->Hope for the long term business
->You can asked for specific states too
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
Thank you because you have been willing to share information with us. we will always appreciate all you have done here because I know you are very concerned with our. гидра онион
ReplyDeleteLove to read it,Waiting For More new Update and I Already Read your Recent Post its Great Thanks. hydra tor
ReplyDelete